Create the wallets
For an example on how to create the server and client keys/certificates see the following metalink note. The examples are created using orapki utility which creates a standard PKCS12 format to store X.509 certificates and private keys.
Note 762286.1 - End To End Examples of using SSL With Oracle's JDBC THIN Driver
Setup OC4J to use JDBC/THIN with SSL
1. Create a java class as follows, and package it up in a JAR file called "JDBCStartup.jar". This startup class file enables Oracle PKI provider dynamically.
/**
*
* add the following lines to your server.xml
<init-library path="<path_to_JDBCSSLSetup.jar>" />
<startup-classes>
<startup-class classname="JDBCSSLSetup" failure-is-fatal="false">
<execution-order>0</execution-order>
</startup-class>
</startup-classes>
*/
import javax.naming.*;
import java.util.*;
import java.security.Security;
import oracle.security.pki.OraclePKIProvider;
import oracle.j2ee.server.OC4JStartup;
/**
* JDBC over SSL setup startup class for OC4J
*/
public class JDBCSSLSetup implements OC4JStartup
{
/**
* Public, no-argument constructor: required by the Oracle startup class spec
*/
public JDBCSSLSetup()
{
}
public String preDeploy(Hashtable args, Context context) throws Exception
{
// instantiate OraclePKIProvider and put it into provider slot #3
Security.insertProviderAt(new OraclePKIProvider(), 3);
System.out.println("JDBCSSLSetup startup class: OraclePKIProvider has been successfully instantiated");
return "ok";
}
public String postDeploy(Hashtable args, Context context) throws Exception
{
return null;
}
}
2. Place the JAR file into $ORACLE_HOME/j2ee/{container-name}/applib directory.
3. Edit $ORACLE_HOME/j2ee/{container-name}/config/server.xml as follows to add the startup class to the container.
<init-library path="../applib/JDBCStartup.jar" />
<startup-classes>
<startup-class classname="JDBCSSLSetup" failure-is-fatal="true" >
<execution-order>0</execution-order>
</startup-class>
</startup-classes>
4. Restart the container as shown below.
> opmnctl stopproc process-type=pas
> opmnctl startproc process-type=pas
5. OAS 10..1.3.x comes with JDBC driver 10.1.0.5 , you will need to use the latest 10g JDBC driver or 11g JDBC driver, to switch to that driver follow the following metalink how to document. You should add the required JAR files below to the shared library along with the JDBC JAR file.
Note 420303.1 - How to Use The Latest Thin JDBC Driver Across All Applications For a 10.1.3.x OAS Container
If you are using 11g database you will also need these 2 JAR files added to the shared library.
- $ORACLE_HOME/jlib/osdt_cert.jar
- $ORACLE_HOME/jlib/osdt_core.jar
- $ORACLE_HOME/jlib/ojpse.jar
<import-shared-library name="oracle.jdbc" min-version="11.1.0.7"/>
7. Now re-start the container to ensure it picks up the latest JDBC driver which should have been done in the note above.
> opmnctl stopproc process-type=pas
> opmnctl startproc process-type=pas
8. Now you can go ahead and create a data source which is using TCPS either through asconsole or manually editing $ORACLE_HOME/j2ee/{container-name}/config/data-sources.xml
Here we will manually edit data-sources.xml and add a managed data source and connection pool to support our SSL setup. We must use the factory class "oracle.jdbc.OracleDriver" as we need to pass properties to the driver.
<managed-data-source
connection-pool-name="TCPSConnectionPool"
jndi-name="jdbc/jdbcSSLDS"
name="jdbc/jdbcSSLDS"/>
<connection-pool name="TCPSConnectionPool">
<connection-factory
factory-class="oracle.jdbc.OracleDriver"
user="scott"
password="tiger"
url="jdbc:oracle:thin:@(DESCRIPTION=(ADDRESS=(PROTOCOL=tcps)
(HOST=beast.au.oracle.com)(PORT=2484))(CONNECT_DATA=(SERVICE_NAME=linux11g)))"
commit-record-table-name="">
<property
name="javax.net.ssl.trustStore"
value="/home/u01/app/oracle/product/1013AS_red/network/admin/wallets/client/ewallet.p12"/>
<property
name="javax.net.ssl.trustStoreType"
value="PKCS12"/>
<property
name="javax.net.ssl.trustStorePassword"
value="myclient123"/>
</connection-factory>
</connection-pool>
In the example above we connect to the database through TCPS for SSL with Encryption and Authentication.
Note: The connect string should include TCPS as shown above.
9. Now in this example we manually edited data-sources.xml so we must re-start the container once again to pick up those changes.
> opmnctl stopproc process-type=pas
> opmnctl startproc process-type=pas
10. Finally we can test our data source using asconsole Data Sources page as shown below.
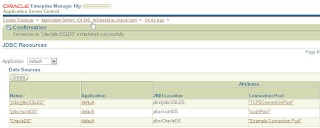
More Information
For more information regarding SSL With Oracle JDBC Thin Driver see the following white paper
http://www.oracle.com/technology/tech/java/sqlj_jdbc/pdf/wp-oracle-jdbc_thin_ssl.pdf
No comments:
Post a Comment